
Post-Quantum Encrypter. Protects your Documents.
The recent research and development of Quantum Computers, based on close atoms behavior, made by different companies as Google, IBM, Intel, IonQ, Microsoft, etc., has meant a substantial scientific advance but also a threat to the present Cybersecurity and encryption systems we use everyday in computers and Information Technologies.
The data security regarding documents and files we use and interchange daily are now exposed, at risk.
It is precisely these large companies that warn about Quantum Computers are able to decipher in some hours the present Cybersecurity systems.
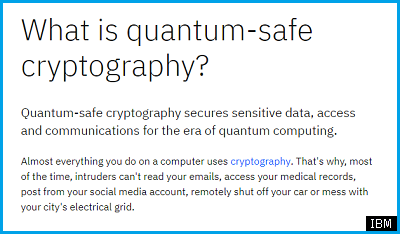 Quantum-Safe Cryptography according to IBM
Quantum-Safe Cryptography according to IBM
|
|
 Quantum Computers and present Cryptography
Quantum Computers and present Cryptography
|
(images taken from: https://www.ibm.com/think/topics/quantum-safe-cryptography)
PQEncrypter is an algorithm for encrypting and decrypting documents and files with the unique feature that it can not be defeated by Quantum Computers, nor by classical computers. Moreover, it turns out to be completely immune to brute-force attacks or by using modern Cryptanalysis techniques.
It is therefore a Cryptographic Algorithm that surpasses the so-called Post-Quantum Cryptography (PQC) Era.
Learn and see about the features of PQEncrypter and how it seamlessly overcomes the Post-Quantum Cryptography (PQC) phenomenon that affects most present Cybersecurity and encryption systems.
- PQEncrypter leaves the PQC phenomenon behind and securely protects your most precious and sensitive documents, even if they were stored on remote Servers in the so-called Cloud.
- PQEncrypter can not be broken by Quantum Computers. Neither can it be done through computation with classical computers, whether very high-level computing, through 'clusters' or grouping of computers, or through the use of GPUs.
- PQEncrypter is fast and easy to use. It's safe and based on mathematical procedures that are different from those used by present Cybersecurity and encryption systems, which are now compromised.
Interested in improving the Cybersecurity of your company and customers?
See the final results of how your protected documents will look once encrypted with our PQEncrypter:
Final look of a document encrypted with PQEncrypter
|
more information:

|




